Connected in 3 easy steps
Check coverage, buy SIMs, get connected.
NEO
Reduce your total cost of ownership with no contracts, intuitive tools and flexible pricing.
Neo’s simple, flexible design empowers your business. Always feel like you are in control of your solution with these great benefits:

Connected in 3 easy steps
Check coverage, buy SIMs, get connected.

Flexible pricing
Our flexible pricing puts you in the driver’s seat.

Secure Cloud-Based
Management Platform
Monitor activity, diagnose anomalies, manage your solution.

No Contracts, or Hidden-Fees
No contracts. No minimums. No setup or cancellation fees.

Pay-Per-Use Model
Pay only for the data you use, and the devices you connect.





John Stanforth, Grid Transmit
| Included Data | Cost Per Month* | Overage Per MB |
|---|---|---|
| 750 KB | $1.00 | $1.00 |
| 10 MB | $5.00 | $1.00 |
| 50 MB | $10.00 | $0.50 |
| 100 MB | $15.00 | $0.15 |
| 500 MB | $20.00 | $0.02 |
| 1 GB | $30.00 | $0.02 |
| 2 GB | $35.00 | $0.02 |
| 5 GB | $60.00 | $0.02 |
*Cost Per Month Per SIM
| Included Data | Cost Per Month* | Overage Per MB |
|---|---|---|
| 750 KB | $1.00 | $1.00 |
| 10 MB | $5.00 | $1.00 |
| 50 MB | $10.00 | $1.00 |
*Cost Per Month Per SIM
Ryan Bowerman, Fleet Monitor
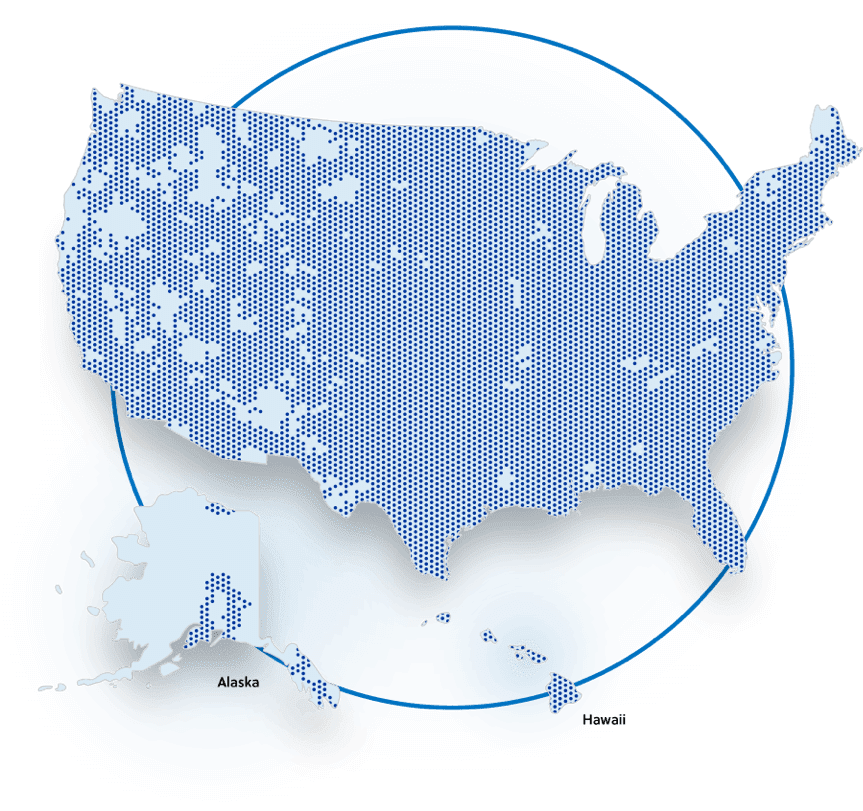
Aeris is the number one wireless communications service provider dedicated to machine-to-machine and IoT in the United States.
Our network offers a combination of GPRS, Edge, and UMTS services to provide extensive GSM and LTE coverage that reaches over 200 million people and many more machines. The high reliability of our network has made Aeris the service provider of choice for the most demanding providers of IoT and M2M solutions. See below for Neo GSM and LTE coverage, which is available in the United States only
John Potpolak, Essi Controls
Start taking advantage of Neo’s simple and flexible pricing today—including no setup fees, no cancellation fees, a pay per use model, access to AerPort, complimentary testing data, and more. Sign up to create your account now.